Reference no: EM131055423
Network Routing and Switching Assignment-
Objectives: This assessment task requires you to demonstrate understanding of basic routing and switching concepts by completing a number of exercise questions. The questions contain
Question 1- Given the following network, construct the routing table of router R1:
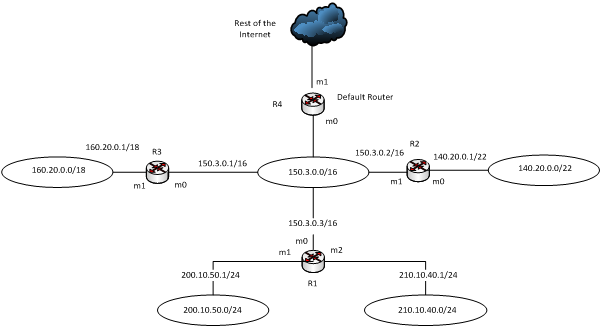
Question 2- An organisation has been granted a block of addresses starting with the address 172.154.60.0/24.
a) Create 4 subnets for this organisation with the first sub-block of 120 addresses, the second sub-block of 60 addresses, the third sub-block of 30 addresses and the fourth sub-block of 12 addresses.
b) How many addresses are left?
Question 3- Consider the following UDP header dump: BB400045003AFF10
a) Identify the source port number.
b) Identify the destination port number.
c) What is the length of the data?
d) Is it a packet from the client to the server or vice versa?
e) What is the client process?
Question 4- Investigate the cloud-managed wireless networks and compile a brief report of around 1400 words. Your references may come from websites, white papers, government documents or published conference or journal papers.
Your report should include only the introduction (about 200 words), body (about 1000 words), conclusion (about 200 words) and the reference list (Do not include the executive summary and table of contents). Use the sub-headings given in the template and include in-text references in the body of the report. Use Harvard style of referencing for the list of references and in-text references.
Marks allocation:
1. Introduction.
2. Architecture.
3. Advantages and disadvantages.
4. Key service providers.
5. Any other relevant information.
Conclusion: A well written coherent conclusion
References: Adherence to Harvard reference style
Question 5- Given the following IPv6 addresses in hexadecimal colon notation, answer the following questions. Where applicable provide your answers in fully expanded hexadecimal colon notation.
a) What is the full (expanded) address of the abbreviated IPv6 address FDEC::CF:0:FFFF?
b) What is the type of block of the abbreviated IPv6 address 2001:A100:FC1::A4B8:AE12:3217:FCBA?
c) What is the type of address of the abbreviated IPv6 address 0::FFFF:194.42.12.7?
|
The main differences between nozick libertarian theory
: 1. Why can Rawls argue that behind the veil of ignorance all people will be able to agree on two principles of distributive justice? How is this relevant to the problem of self-interest?
|
|
Dividends-received deduction for dividends
: For purposes of computing a corporation's state taxable income, do states generally, permit a UnitedStates parent corporation to claim a dividends-received deduction for dividends received from a foreigncountry subsidiary?
|
|
Compare and contrast two pieces of baroque music
: ompare Vivaldi's "The Spring" Concerto with Bach's "Brandenburg Concerto No. 5." Focus your discussion on the musical characteristics that can be heard in the music, including form, genre, and unique characteristics. Be sure to highlight any simil..
|
|
Have you had any experience with knowledge-based tension
: Have you had any experience with this knowledge-based tension between staff and IT? Even if you haven't, can you see how it could be a problem? What should we be doing about it?
|
|
Identify the source port number
: COIT20261 Network Routing and Switching Assignment. Consider the following UDP header dump: BB400045003AFF10. Identify the source port number. Identify the destination port number. What is the length of the data
|
|
Prepare the acquisition analysis
: 1. Prepare the acquisition analysis as of acquisition date. Compute the unamortized differential as of 1/1/2013. 2. Analyze each intercompany transaction. Label as either upstream downstream.
|
|
Purpose of corporate sustainability reporting
: Provide a report summarising the purpose of Corporate Sustainability Reporting (CSR) by referring to the Global Reporting Initiatives' (GRI) Sustainability Framework
|
|
Identify the circumstances surrounding each issue
: Create a SWOT table summarizing your findings. Your environmental analysis should consider, at a minimum, the following factors. For each factor, identify the one primary strength, weakness, opportunity, threat, and trend, and include it in your t..
|
|
Write a paper about the products of the company dove
: Write a paper about the products of the company Dove. Recomendations about the products of DOVE to the company Unilever.
|