Reference no: EM131319631
Question 1
Which of the following must you do before IP source guard can be used on a switch port? (Select 2 choices.)
A) Enable IP routing on the switch port.
B) Enable DHCP snooping on the switch.
C) Configure static IP bindings on the switch.
D) Enable uRPF on the switch port.
Question 2
Which of the following technologies can you use to bundle redundant links to form a single robust link? (Select the best answer.)
A) EtherChannel
B) StackWise
C) VTP
D) HSRP
Question 3
You administer the network shown below.
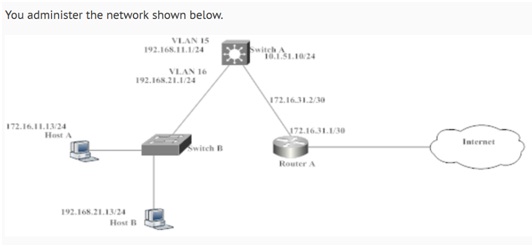
Which of the following should you configure as the default gateway on HostA to enable HostA to access the Internet? (Select the best answer.)
A) 192.168.21.1/24
B) 172.16.11.1/24
C) 10.1.51.10/24
D) 172.16.41.1/24
E) 10.1.51.5/24
F) 172.16.31.1/30
Question 4
Which of the following are required for interVLAN routing? (Select 2 choices.)
A) a Layer 3 switch connected via a trunk link to a router with SVIs configured
B) a Layer 2 switch connected via a trunk link to a router with subinterfaces configured
C) a Layer 2 switch with IP routing enabled and subinterfaces configured
D) a Layer 3 switch with IP routing enabled and SVIs configured
Question 5
Which of the following commands should you issue to convert a switched interface to a routed interface? (Select the best answer.)
A) switchport nonegotiate
B) switchport mode trunk
C) switchport mode access
D) no switchport
Question 6
Which of the following statements are true regarding PVLANs? (Select 2 choices.)
A) Primary VLANs must be configured as isolated or community VLANs.
B) Routers, firewalls, and gateways should be connected to promiscuous ports.
C) A switch must be configured for VTP transparent mode to support private VLANs.
D) Community VLANs can communicate with both promiscuous and isolated ports.
E) Promiscuous ports can service multiple primary VLANs.
Question 7
Refer to the exhibit.
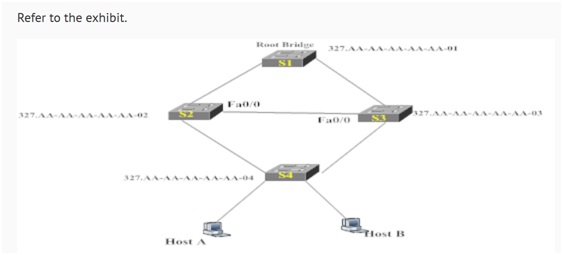
The network you administer consists of the devices shown in the exhibit. Each link is 100 Mbps and is connected to a Fast Ethernet port. Switch S1 is the root bridge. You enable root guard on Fa0/0 on switch S2 and switch S3 by issuing the spanning-tree guard root command in interface configuration mode on both switch ports. You also enable the Uplinkfast feature on S2 and S3 by issuing the spanning-tree uplinkfast command in global configuration mode on both switches.
Which of the following statements best describes what will occur if the link between S1 and S2 is broken? (Select the best answer.)
A) Spanning tree will be disabled.
B) Only Fa0/0 on S2 will be put into the root-inconsistent (blocked) state.
C) Traffic will follow its normal path from HostB to S1.
D) The Fa0/0 port on both switches will be put into the root-inconsistent (blocked) state.
E) Only Fa0/0 on S3 will be put into the root-inconsistent (blocked) state.
Question 8
Your company's network includes a switch named Switch1 that is connected to a router named Router1 using FastEthernet 0/1 on the switch. Router1 is the default gateway for all hosts in the network. You have issued the following commands on Switch1:
Switch1(config)#vlan 100
Switch1(config-vlan)#private-vlan isolated
Switch1(config-vlan)#end Switch1(config)#vlan 200
Switch1(config-vlan)#private-vlan community
Switch1(config-vlan)#end
Switch1(config)#vlan 300 Switch1(config-vlan)#private-vlan primary Switch1(config-vlan)#private-vlan association 100,200
Switch1(config-vlan)#end
You now want to associate the FastEthernet 0/1 port on Switch1 with the private VLAN.
Which of the following commands should you issue on the interface? (Select 2 choices.)
switchport private-vlan host association 300 100
switchport mode private-vlan promiscuous
switchport private-vlan host association 300 200
switchport private-vlan mapping 300 100,200
switchport mode private-vlan host
Question 9
From the list below select two best features of GLBP.
In a GLBP group, only one AVG can be assigned but multiple AVFs can be assigned.
One router is elected as the active router, and another router is elected as the standby router.
In a GLBP group, multiple AVGs can be assigned but only one AVF can be assigned.
One router is elected as the master router, and all other routers are placed in the backup state.
In a GLBP group, only one AVG and only one AVF can be assigned.
All routers in a GLBP group can participate by forwarding a portion of the traffic.
Question 10
Which of the following is the phase during which the IP SLA source device begins to send test packets to the IP SLA responder device? (Select the best answer.)
A) the monitoring phase
B) the response phase
C) the probing phase
D) the control phase
Question 11
Which of the following commands should you issue to enable AAA on a switch? (Select the best answer.)
A) aaa authentication
B) aaa authorization
C) aaa new-model
D) aaa accounting
Question 12
You are configuring a private VLAN on a switch. You issue the following command sequence on the switch:
Switch(config)#vlan 5
Switch(config-vlan)#private-vlan isolated
Switch(config)#vlan 10
Switch(config-vlan)#private-vlan primary
Switch(config-vlan)#private-vlan association add 5
Then you issue the following command sequences on interfaces FastEthernet 0/1 and FastEthernet 1/1 on the switch:
Switch(config)#interface fastethernet 0/1
Switch(config-if)#switchport mode private-vlan host
Switch(config-if)#switchport private-vlan host-association 10 5
Switch(config)#interface fastethernet 1/1
Switch(config-if)#switchport mode private-vlan promiscuous
Switch(config-if)#switchport private-vlan mapping 10 5
Which of the following statements is true about this configuration? (Select the best answer.)
A) A host connected to VLAN 5 will be able to reach only VLAN 10.
B) A host connected to another isolated VLAN will be able to communicate with a host connected to VLAN 5.
C) A host connected to VLAN 5 will be able to reach only other hosts connected to VLAN 5.
D) A host connected to VLAN 5 will not be able to access any other VLANs.
Question 13
Which of the following describes why you should use SSH on Cisco switches when possible? (Select the best answer.)
A) SSH is the only supported connection protocol on some switches.
B) SSH disables access to unused switch ports.
C) SSH provides encryption, whereas Telnet does not.
D) SSH requires user names, whereas Telnet does not.
Question 14
You issue the following commands on a switch named SwitchA:
SwitchA#configure terminal
SwitchA(config)#interface Fa0/0
SwitchA(config-if)#switchport port-security
SwitchA(config-if)#switchport port-security maximum 12
You want to configure SwitchA to disable interface Fa0/0 and send an SNMP trap message when more than 12 MAC addresses are learned on the interface.
Which of the following commands should you issue? (Select the best answer.)
A) switchport port-security violation shutdown
B) switchport port-security violation restrict
C) switchport port-security violation protect
D) switchport port-security violation disable
Question 15
At what layer do FHRPs operate? (Select the best answer.)
A) both Layer 2 and Layer 3
B) Layer 1
C) Layer 3
D) Layer 2
Question 16
Which of the following statements is true regarding SSO? (Select the best answer.)
A) The active and standby devices must run identical IOS software versions.
B) SSO requires RRI.
C) SSO transfers the crypto configuration from the active device to the standby device.
D) HSRP cannot be used with SSO.
Question 17
A portion of your company's network is shown below:
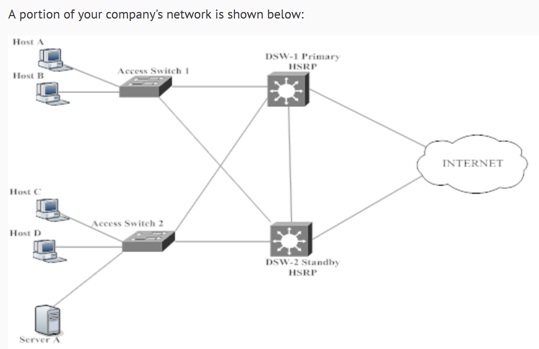
If HSRP is not properly configured on DSW2 and DSW1 becomes unavailable, which of the following is most likely to occur? (Select the best answer.)
A) Host A might not be able to ping Host B.
B) Host C might not be able to access Server A.
C) Host A might not be able to access the Internet.
D) Host C might not be able to ping DSW2.
Question 18
Which of the following is the phase of IP SLA communications between a source and a responder during which packets are sent over UDP port 1967 by default?
(Select the best answer.)
A) the monitoring phase
B) the control phase
C) the probing phase
D) the response phase
Question 19
You administer a network that uses four routers configured as an HSRP group to provide redundancy for the gateway. You issue the show running config command from privileged mode on each router and receive the following outputs:
RA# show running config RB#show running config
Host name RA Host name RB
Interface Serial0/0 Interface Serial0/0
Ip address 10.10.1.1 255.255.255.0 Ip address 10.10.1.2 255.255.255.0
Standby priority 200 Standby priority 150
RC# show running config RD#show running config
Host name RC Host name RD
Interface Serial0/0 Interface Serial0/0
Ip address 10.10.1.3 255.255.255.0 Ip address 10.10.1.4 255.255.255.0
Standby ip 10.10.1.10 Standby ip 10.10.1.10
Standby priority 150 Standby priority 100
Based on the output for each router, which of the following statements is true? (Select the best answer.)
A) RA should act as the active router, and RC should act as the standby router.
B) RB should act as the active router, and RA should act as the standby router.
C) RD should act as the active router, and RA should act as the standby router.
D) RC should act as the active router, and RD should act as the standby router.
E) RA should act as the active router, and RB should act as the standby router.
F) RB should act as the active router, and RC should act as the standby router.
Question 20
From the choices given below, Identify two tables embedded in Cisco Express forwarding.
A) Cisco express forwarding Table
B) Forwarding information table
C) Adjacency table
D) Forwarding information base
E) Link state table
Question 21
When a multilayer switch is connected directly to several hosts, the FIB table on the switch maintains a prefix for the subnet rather than for the individual host prefixes. Associate this statement with the choices given below. (Select the best answer)
A) Punt adjacency
B) Subnet adjacency
C) Connected adjacency
D) Glean adjacency
Question 22
Select the statement listed below which describes best the relationship between the data center and the core layer?
(Select the best answer)
A) The data center devices physically connect directly to the enterprise core layer switches.
B) The data center devices physically connect directly to the enterprise distribution layer switches
C) The data center devices physically connect to access switches
D) The data center devices connection model is different from the 3 Layer model used for the enterprise network.
Question 23
Which two devices can be used to configure a WLAN using controller-based Aps?
A) Cisco WCS
B) Cisco WLSE
C) WLC
D) AP
Question 24
Which protocol supports split-MAC operation for the Cisco Lightweight WLAN solution?
A) CCKM
B) LWAPP or CAPWAP
C) WLCCP
D) SNMP
Question 25
Which two wireless components are used for the standalone WLAN solution? (Choose 2)
A) WLC
B) ACS
C) Cisco Works WLSE
D) WCS
Question 26
Choose two statements which are not true about SSID.
A) SSIDs on client and AP must match
B) SSIDs are not case sensitive
C) A client can be configured without an SSID
D) SSIDs on all Aps must be identical
Question 27
How does video traffic compare to VoIP traffic? (Select the best answer)
A) Video is bandwidth intensive, just like voice.
B) Video is delay sensitive, just like voice.
C) Video needs steady packet transmission, just like voice.
D) All of the above are correct.
Question 28
Which is a common QoS configuration on access ports to IP phones?
A) switchport trust cisco-phone
B) mls qos trust device cisco-phone
C) switchport qos trust cisco-phone
D) power inline trust autodetect
Question 29
Which protocol allows creating a CoS in the 802.1Q trunking protocol?
A) ISL
B) 802.1p
C) 802.1d
D) No protocol; CoS is part of 802.1Q
Question 30
What would an attacker do to perform a switch spoofing attack?
A) Send random ARP requests to the connected stations.
B) Flush the switch CAM to force it to flood.
C) Source all its frames with the address FF:FF:FF:FF:FF:FF.
D) Mark its frames with ISL or 802.1Q
Question 31
What is the role of the switch in a AAA architecture?
A) Authentication server
B) Supplicant
C) Authenticator
D) RADIUS entry point