Reference no: EM132138201
Assignment Description
Project Scope: A typical network layout diagram of a firm is given below for illustrative purposes only. The service requirements are enclosed.
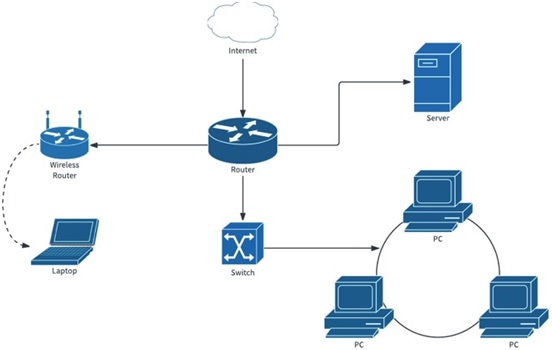
Figure. Network layout of a firm
Service requirements
1. 5 departments with 5 subnets. Only admin, HR and the finance department will have all the access to the services available. Engineering and sales have access to the print server and file server but not to the finance department.
2. IP network design
3. Hardware requirements with costs specification
4. Configuration details on the hardware (Routers and Switches)
Report requirements: The report should have a detail explanation of the planning and designing of the network. It is recommended that bullet points are only included whenever necessary.
1. Project Scope
2. Project requirements
3. Network design - Consider the human factor design concepts
4. IP addressing in a tabular form (include justification whenever necessary)
5. Network topology diagram (Netsim preferred)
- Switch configuration
- Router configuration
- DHCP configuration
- The access point and server configuration guidelines
- Security configuration
Note: Student should show the demo of the network design in Week 11 lab. Demonstration marks will be awarded in regards to the stage of the completion of the design.
Note: Programme should run on cisco and need two different answers for this assignment.
Note: Need to do Only Netsim Part