Reference no: EM131156728
Question 1 of 5:
a) Suppose you are evaluating two hardware lease proposals. Option 1 costs $10,000, but requires that the entire amount be paid in advance. Option 2 costs $14,000, but the payments can be made $2,000 now and $2,000 per year for the next six years. If you do a present value analysis assuming a 15 percent discount rate, which proposal is less expensive?
*** For this question, please limit you response to a maximum of two pages.
Justify all your numerical answers and answer all the questions using your own words.
Show all your work, including how you found your answer (this is very important and
essential to have your answer graded appropriately!).
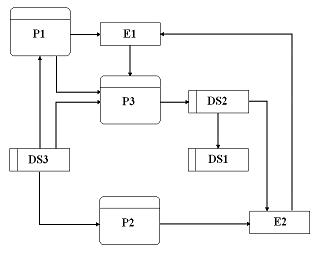
b) In the following proposed DFD design, there are some typical errors among external entities (E), processes (P) and data stores (DS). Identify and explain any errors in the following design.
a) You are a project manager at L & D Inc., specialized in information technology and network engineering. One of your junior systems analyst came to you for an advice of a technology to capture user information requirements. He described to you that he had talked with his client several times in the past week to define user information requirements. Each time he thought he had captured user information requirements, they've already changed. Finally, he thinks his clients do not even know what they want for their system.
Give your junior systems analyst an advice of a technology that he could use to capture user information requirements and explain to him how this technology can help him to better define users' information requirements.
*** For this question, please limit you response to a maximum of one page.
Clarification:
Students should take the word "technology" as being defined in several dictionaries as a scientific method, technique, theory, or practice to solve a practical problem. I copy here some definitions of the word "technology" from several dictionaries that you might refer to answer your question.
1. The application of science, especially to industrial or commercial objectives.
2. The scientific method and material used to achieve a commercial or industrial objective.
3. The application of practical sciences to industry or commerce.
4. The methods, theory, and practices governing such application a highly developed technology.
1. The use of scientific knowledge to solve practical problems, especially in industry & commerce.
2. The specific methods, materials, and devices used to solve practical problems.
Question 2 of 5:
Mr. Smith, who owns a furniture company, wants to develop an information system for tracking shipments to warehouses. Using the data from the table below, please do the following:
1. Draw a Gantt chart (learned from this course) to help Mr. Smith organize his design project.
2. When is it appropriate to use a Gantt chart? What are the disadvantages?
3. Drawn a PERT diagram (learned from this course) and then list all paths, calculate and identify the critical path.
*** For this question, please limit you response to a maximum of two pages.
|
Description
|
Task
|
Must Follow
|
Time (Weeks)
|
|
Generate data flow
|
A
|
None
|
7
|
|
Build decision tree
|
B
|
A
|
4
|
|
Build data dictionary
|
C
|
B
|
10
|
|
Write up project
|
D
|
C and H
|
4
|
|
Design output prototype
|
E
|
None
|
2
|
|
Revise output design
|
F
|
E
|
9
|
|
Write use cases
|
G
|
None
|
10
|
|
Design database
|
H
|
G and F
|
8
|
Question 3 of 5: (20 points)
A summary of business activities for registering courses for enrolled students
and for registering class lists for faculty members and administrators at an
online university is as follows:
Students log into a system with their "user name and password" that is validated by a secure logon system handled by a "Network and Security" department. Students then send in a course registration form consisting of their personal information and their desired courses. The system checks that the courses are available and that the student is academically qualified to take the course.
Students could pay for their courses by credit cards or they could pay through the Federal Student Aid (FAFSA), if qualified. For the FAFSA students, the system checks with the "Business" department to see if the student is financially qualified to take the course. For credit cards, the system validates students' credit card information through a credit card company and generated appropriate status message to students.
Based on the checking results, the system will send to the student a confirmation and/or rejection letter for each requesting course with detailed information of what to do next in either case. In addition, for any rejection cases, the system will also notify the Counselor department so students could arrange appointments to talk with their counselors to resolve their issues, if possible.
Draw a context diagram for the "Courses Registration" system.
Question 4 of 5:
Draw an entity-relationship diagram (ERD) in the third normal form for a "student database record" system based on the following situation:
- A student may register for many courses, and a course may have many students.
- A student may have many professors, and a professor may teach many students.
- A student is assigned only one counselor, but each counselor usually has many students.
Identify relationships among the diagram entities as "one-to-one" and/or "one-to-many", if any. Identify entities as "entity" or "associative entity".
Question 5 of 5:
Consider a research management system in which faculty members from different departments are often collaborated to a research project. Each faculty member
is allocated with a certain amount of research fund. The following is an
example of an un-normalized RESEARCH-DATA table for two research projects.
RESEARCH-DATA
|
Research ID
|
Research Name
|
Start Date
|
Faculty ID
|
Faculty Name
|
Research Fund
|
Department ID
|
Department Name
|
|
1
|
E-Commerce
|
04/10/2015
|
2489
|
Smith
|
$200,000
|
1
|
ITEC
|
|
|
|
|
1887
|
Jones
|
$5,000
|
1
|
ITEC
|
|
|
|
|
9540
|
Mike
|
$25,000
|
5
|
ISAS
|
|
2
|
Cloud Computing
|
12/15/2015
|
3436
|
Catherine
|
$200,000
|
2
|
BUS
|
|
|
|
|
2489
|
Smith
|
$10,000
|
1
|
ITEC
|
Perform the normalization process to convert the above un-normalized table to:
1. First normal form (1NF)
2. Second normal form (2NF)
3. Third normal form (3NF)
Please show all your work. Please show each step along the way and identify primary keys, if any, in each table in each step.