Reference no: EM132203135
Network Analysis using Wireshark
Purpose of the assessment (with ULO Mapping) This assignment is designed to develop deeper analytical understanding of different distributed network conditions.
At the completion of this assessment students should be able to:
d. Analyse performance and deployment issues for networked applications;
e. Compare appropriate industry tools and techniques to manage networked applications;
Assignment Description
The aim of the assignment is to develop an analytical understanding of performance and management of different types of networked applications. The assignment will provide an opportunity to understand network performance and management issues of networked applications using state of the art tools. These exercises provide an opportunity to demonstrate analytical ability of evaluating distributed systems performance, Quality of Service and service management.
Overview and General Instructions of Assignment
Students need to form a group of two in their own lab class and inform tutor about their group during Week 7 Lab. Each group will need to capture packets on their home network and at MIT while accessing the following websites. One website is of a news channel and the other one is a website for live streaming. The students are required to capture packets of multiple images from the news channel website and capture packets from the live stream website while streaming for 10 minutes once at MIT in a group and then on their home network individually. So at the end there will be six trace files, three for each website, two captured on MIT network and four on students' home networks.
Part 1:
The first part of the report should be about general statistics of all six captures using Wireshark that must include:
1. Time of capture
2. Total number of captured packets
3. IP addresses of the client and server
Part 2:
The second part of the report must include screen shots of packet capture, screenshots of different statistics from Wireshark and complete analysis of those screenshots for both websites for all three networks. Only screenshots of the graphs or other statistics will not get any marks as those must be analysed in detail to discuss the quality of service for a particular application. The students are required to analyse the network performance for the assigned websites considering following aspects:
1. Throughput
2. Round Trip Time
3. TCP retransmissions
While collecting statistics please make sure, you are looking at the right flow as your Wireshark file may have packets from other applications and flows as well. Figure 1 on next page shows the throughput graph generated by Wireshark and source and destination addresses are clearly shown. You need to collect statistics for flows which are from server to client.
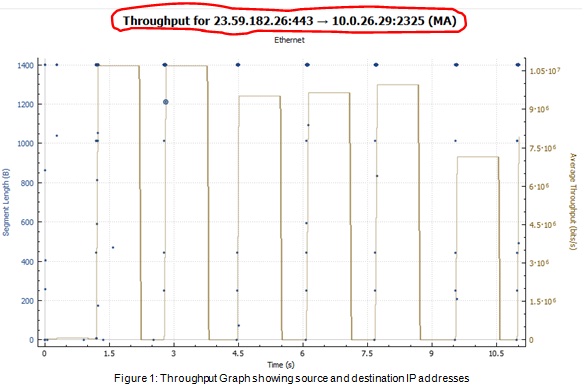
To see the TCP retransmissions you need to enter the following filter in Wireshark: tcp.analysis.retransmission
Part 3:
The third part of the report is about comparing the collected Wireshark statistics of the two different networked applications on three different networks. The throughput graphs and TCP retransmission statistics for web page transfer and live streaming (provided in part 2) need to be compared with each other and for all three networks. The differences of the performance to be identified and reasons must be provided for such differences.
Part 4:
Students need to download, install, use and compare another free network performance measurement tool from the Internet on their home computer. One possible option is Microsoft Message Analyzer. The tool should be used to analyse the network traffic captured while accessing one of the news websites mentioned in Table 1.
The chosen tool should be compared with Wireshark on the basis of following criteria:
1. Ease of access and use: how easy it is to download, install and start using (any changes to be made to the system etc.) as compared to Wireshark
2. GUI: Compare at least four GUI features of the chosen tool with Wireshark
3. Visualisation of traffic: After capturing packets by the chosen tool the effectiveness of the visualisation of the network traffic should be compared with Wireshark.
4. Statistics generation: At least one statistics like throughput, RTT etc. needs to be generated by the chosen tool and to be compared with the same generated by Wireshark.