Reference no: EM131434737
Homework: Network Consultation for Design IT
This assignment contains two Sections: Network Consultation Proposal and Network Consultation Presentation. You must submit both sections as separate files in order to complete this assignment.
The owners of Design IT, who recently purchased 56'x36' space for their expanding business, have asked you to place a bid on a consulting job. Design IT is a graphic arts company that, up until now, had contracted work out to temporary design services. The new space will allow them to hire two full time designers and a receptionist.
Description of space purchased:
- 4 Cubicles
- 1 Office
- 1 Server room
- 1 Reception desk
- 1 Conference room
Below is the design of the space purchased
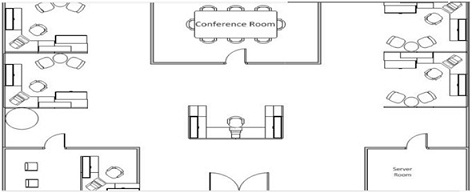
Using the building layout, your role is to provide Design IT with a network design that interconnects the following considerations:
- Design IT plans to relocate three servers already configured as follows:
o 1 Web Server - Microsoft IIS Server
o 1 File Server - Microsoft Server 2008
o 1 Server - Server 2008 Small Business Server
Design IT has requested that the design include the following:
o High speed Internet access
o Firewall
o Antivirus / malware protection
o Six computers
o Three color laser printers
o Wireless access for portable devices
Design IT has requested the consideration of all interconnected devices and wiring, along with speeds, for best performance.
Section 1: Network Consultation Proposal
(Microsoft Word)
Create a cost analysis, and develop a proposal for the company.
1. Write a five to seven page proposal in which you:
a. Recommend one suitable network design.
b. Suggest one network architecture.
c. Suggest LAN and Wireless LAN (WLAN) wiring considerations.
d. Recommend hardware options and costs.
e. Suggest security considerations for:
i. Firewall
ii. Antivirus software
f. Recommend software options and costs.
g. Outline the labor costs, equipment costs, and service costs for your suggested design in table format.
h. Identify the single point of failure, and recommend potential mitigation strategies.
i. Use at least three quality resources in this assignment. Note: Wikipedia and similar Websites do not qualify as quality resources.
Section 1 of your assignment must follow these formatting requirements:
- Be typed, double spaced, using Times New Roman font (size 12), with one-inch margins on all sides; citations and references must follow APA or school-specific format. Check with your professor for any additional instructions.
- Include a cover page containing the title of the assignment, the student's name, the professor's name, the course title, and the date. The cover page and the reference page are not included in the required assignment page length.
Section 2: Network Consultation Presentation
(Microsoft PowerPoint or equivalent)
Use Microsoft PowerPoint or an open source alternative to present your findings to the client.
2. Create a five to ten slide presentation in which you:
a. Outline the recommendations from your written proposal in Section 1.
b. Provide general speaking notes that you would use to highlight non-visual content.
The specific course learning outcomes associated with this assignment are:
- Explain the basic components and media of network systems and distinguish between LANs, MANs, and WANs.
- Summarize current networking standards and how standards bodies and the standardization process impact networking technology.
- Describe the TCP / IP protocols and various functions among the application layer.
- Contrast why different technologies are deployed in different contexts of networking, such as topology, bandwidth, distance, and number of users.
- Explain and differentiate among network hardware devices and components.
- Compare and contrast among network operating systems.
- Describe security policy, practices, encryption techniques, and design considerations in support of business operations in a networked environment.
- Explain the role of integrity and availability in a networked environment.
- Use technology and information resources to research issues in computing networks.
- Write clearly and concisely about introductory networking topics using proper writing mechanics and technical style conventions.