Reference no: EM13804019
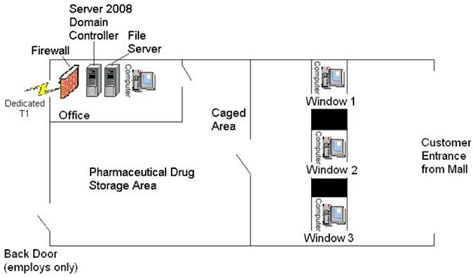
You are the Information Security Officer for a small pharmacy that has recently been opened in the local shopping mall. The daily operation of a pharmacy is a unique business that requires a combination of both physical and logical access controls to protect medication and funds maintained located on the premises and personally identifiable information and protected health information of your customers.
Your supervisor has tasked you with identifying inherent risks associated with this pharmacy and establishing physical and logical access control methods that will mitigate the risks identified.
1) Firewall
2) Desktop computers
3) Windows 2008 Active Directory Domain Controllers (DC)
4) Dedicated T1 Connection (1)
5) File Server
Write a ten to fifteen (10-15) page paper in which you:
1. Identify and analyze any potential physical vulnerabilities and threats that require consideration.
2. Identify and analyze any potential logical vulnerabilities and threats that require consideration.
3. Illustrate in writing the potential impact of all identified physical vulnerabilities and threats to the network and the pharmacy.
4. Identify all potential vulnerabilities that may exist in the documented network.
5. Illustrate in writing the potential impact of all identified logical vulnerabilities to the network and the pharmacy.
6. For each physical vulnerability and threat identified, choose a strategy for dealing with the risk (i.e., risk mitigation, risk assignment, risk acceptance, or risk avoidance).
7. For each logical vulnerability and threat identified, choose a strategy for dealing with the risk (i.e., risk mitigation, risk assignment, risk acceptance, or risk avoidance).
8. For each physical vulnerability and threat identified, develop controls (i.e., administrative, preventative, detective, and corrective) that will be used to mitigate each risk.
9. For each logical vulnerability and threat identified, develop controls (i.e., administrative, preventative, detective, and corrective) that will be used to mitigate each risk.